| | Published May 9th, 2012
| Managing Your Child's Reputation in the Digital Age
| | Laurie Snyder | 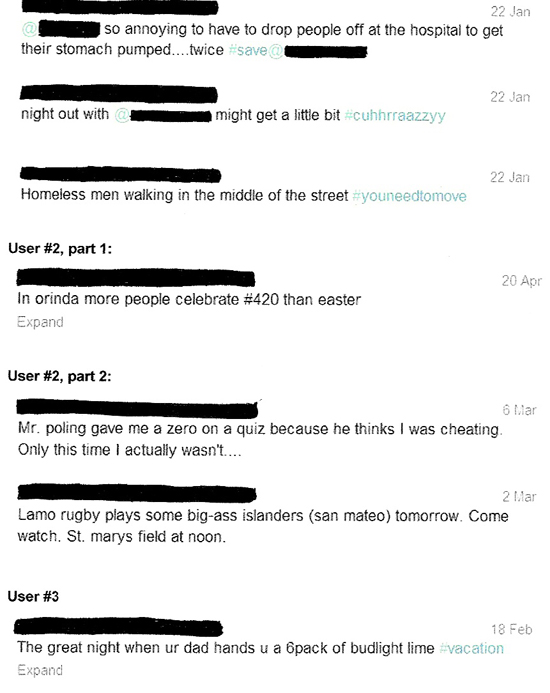 | | Tweeting teens can not only hurt their own images, but can inadvertently stain the reputations of family and friends. Many are unaware that they have been mentioned in questionable posts by someone they trust. (The names of the Twitter users and their friends and families have been blacked out.)
|
It is the age-old conundrum. How do parents let kids spread their wings - but not so much that they'll be hurt before they're able to soar? It was hard enough when parents "just" had to worry about teens driving drunk or too fast. But now, parents must deal with an added burden - the rise of social media.
 In today's world, online bullies push classmates toward suicide by 'sexting' compromising photos. Naive teens Tweet about drug use, and overeager tech firms re-post everything without permission from the minors or their parents.
In today's world, online bullies push classmates toward suicide by 'sexting' compromising photos. Naive teens Tweet about drug use, and overeager tech firms re-post everything without permission from the minors or their parents.
 Think it doesn't happen here? Think again.
Think it doesn't happen here? Think again.
 In April, one Lamorindan posted: "i do poppers all the time."
In April, one Lamorindan posted: "i do poppers all the time."
 And an 18-year-old Tweeted, "[Bleep] the Adderall. Give me Xanax and Valium right now. I'm on the verge of a mental breakdown."
And an 18-year-old Tweeted, "[Bleep] the Adderall. Give me Xanax and Valium right now. I'm on the verge of a mental breakdown."
 Both local residents also have profiles on Klout.com - a company that tracks Tweets and Facebook posts and builds individual profiles, which include users' Twitter photos and links to people Klout decides are users' "influencers." Klout's practices recently came under fire after parents uncovered profiles of children on the site.
Both local residents also have profiles on Klout.com - a company that tracks Tweets and Facebook posts and builds individual profiles, which include users' Twitter photos and links to people Klout decides are users' "influencers." Klout's practices recently came under fire after parents uncovered profiles of children on the site.
 Other Lamorinda students' profiles are on the site as well.
Other Lamorinda students' profiles are on the site as well.
 In its 2011 study, "Teens, Kindness and Cruelty on Social Network Sites," Pew Internet states that 95 percent "of all teens ages 12-17 are now online," and that 88 percent have witnessed cyber-cruelty.
In its 2011 study, "Teens, Kindness and Cruelty on Social Network Sites," Pew Internet states that 95 percent "of all teens ages 12-17 are now online," and that 88 percent have witnessed cyber-cruelty.
 As for parents, 80 percent "who use social media and who also have a child who uses social media have friended their child." However, only 66 percent have checked out what has been posted about their kids, and just 54 percent use "parental controls or other means of blocking, filtering, or monitoring."
As for parents, 80 percent "who use social media and who also have a child who uses social media have friended their child." However, only 66 percent have checked out what has been posted about their kids, and just 54 percent use "parental controls or other means of blocking, filtering, or monitoring."
 Orinda Intermediate School counselors Jay Stevens and Heather Raser posted a resource list on the OIS web site for parents who are looking to take a more active role monitoring their kids. "While some parents simply do not allow their 12-year-old child to have access to social networking sights . . . other parents monitor their child's internet use with extreme vigilance," Stevens says. "Developmentally, middle school students are often not mature enough to [manage Facebook/MySpace]. As a result, social networking sites can easily become breeding grounds for social drama among children."
Orinda Intermediate School counselors Jay Stevens and Heather Raser posted a resource list on the OIS web site for parents who are looking to take a more active role monitoring their kids. "While some parents simply do not allow their 12-year-old child to have access to social networking sights . . . other parents monitor their child's internet use with extreme vigilance," Stevens says. "Developmentally, middle school students are often not mature enough to [manage Facebook/MySpace]. As a result, social networking sites can easily become breeding grounds for social drama among children."
 Owen Tripp, Chief Operating Officer of Reputation.com agrees, but notes, "By eight years old, you should really be having a conversation with your kid about how to create an Internet ID."
Owen Tripp, Chief Operating Officer of Reputation.com agrees, but notes, "By eight years old, you should really be having a conversation with your kid about how to create an Internet ID."
 Tripp co-founded the online reputation management company with Michael Fertik in 2006. "It was a moment several years ago where we were looking at stories of cyber-bullying," Tripp says. Disturbed by photos and posts that were destroying teens' sense of well being, they realized that "every other company was interested in more pictures, more data, more comments." Users forget, he says, that social media was "not designed with the user at the center" but built to make everyone's data publicly available for advertisers.
Tripp co-founded the online reputation management company with Michael Fertik in 2006. "It was a moment several years ago where we were looking at stories of cyber-bullying," Tripp says. Disturbed by photos and posts that were destroying teens' sense of well being, they realized that "every other company was interested in more pictures, more data, more comments." Users forget, he says, that social media was "not designed with the user at the center" but built to make everyone's data publicly available for advertisers.
 Now, advertisers aren't the only ones looking. One Stanford University dean told Tripp that everyone admitted has been Googled. And, according to William R. Fitzsimmons, Dean of Admissions and Financial Aid to Students at Harvard College:
Now, advertisers aren't the only ones looking. One Stanford University dean told Tripp that everyone admitted has been Googled. And, according to William R. Fitzsimmons, Dean of Admissions and Financial Aid to Students at Harvard College:
 "The Harvard Admissions Office generally does not proactively seek information about applicants online. However, applicants often point us to their websites or to other information online to supplement their application materials. That said, we may have occasion to encounter an applicant's digital footprint. This often can be positive for applicants to the degree that it helps demonstrate their range of interests and accomplishments, but could be negative if it raises serious questions about character or judgment."
"The Harvard Admissions Office generally does not proactively seek information about applicants online. However, applicants often point us to their websites or to other information online to supplement their application materials. That said, we may have occasion to encounter an applicant's digital footprint. This often can be positive for applicants to the degree that it helps demonstrate their range of interests and accomplishments, but could be negative if it raises serious questions about character or judgment."
 So what should parents do?
So what should parents do?
 Set privacy controls for children well into their teens. Don't just friend kids; Google them. Find out what they're doing - and what their friends and others are posting about them.
Set privacy controls for children well into their teens. Don't just friend kids; Google them. Find out what they're doing - and what their friends and others are posting about them.
 The average youngster, Tripp says, has 2.1 Facebook pages - the "pigtails, apple pie" version - and the one kids actually use. Some even create third profiles. Introverted kids pretend to be athletes. Others explore their sexuality.
The average youngster, Tripp says, has 2.1 Facebook pages - the "pigtails, apple pie" version - and the one kids actually use. Some even create third profiles. Introverted kids pretend to be athletes. Others explore their sexuality.
 What teens and parents don't understand, warns Tripp, is that Facebook and other companies "fingerprint" every single account, enabling most anyone to track multiple accounts back to the same user. "So, when you're going out for a job, there's all this other interesting information that you've published about yourself."
What teens and parents don't understand, warns Tripp, is that Facebook and other companies "fingerprint" every single account, enabling most anyone to track multiple accounts back to the same user. "So, when you're going out for a job, there's all this other interesting information that you've published about yourself."
 Patty Bishop, Director of Career Planning and Placement at Saint Mary's College, confirms this. She counsels students not to post anything that would make their grandmothers blush, explaining how a senior at another campus who landed a job had the offer rescinded when the well-known firm found profanity on his Facebook page.
Patty Bishop, Director of Career Planning and Placement at Saint Mary's College, confirms this. She counsels students not to post anything that would make their grandmothers blush, explaining how a senior at another campus who landed a job had the offer rescinded when the well-known firm found profanity on his Facebook page.
 As for Tweeting about drug use, Bishop describes it as a deal breaker. "Do not be fooled into thinking that your Facebook isn't being looked at."
As for Tweeting about drug use, Bishop describes it as a deal breaker. "Do not be fooled into thinking that your Facebook isn't being looked at."
 "Anyone thinking of applying to college," adds Fitzsimmons, "should always keep in mind that information posted online can last a lifetime."
"Anyone thinking of applying to college," adds Fitzsimmons, "should always keep in mind that information posted online can last a lifetime."

|
 Digital Safety 101
Digital Safety 101

 Watch out for "foolish friends," as well as "stranger danger."
Watch out for "foolish friends," as well as "stranger danger."

 Select sensible user names and profile photos. Work with children to set privacy settings (for everything, including gaming sites). Have them friend you. Google them.
Select sensible user names and profile photos. Work with children to set privacy settings (for everything, including gaming sites). Have them friend you. Google them.

 Be sure kids interact on social media only with friends they know. (Flags: Followers living more than 10 miles away, with significantly older birth dates, LinkedIn users following young teens.)
Be sure kids interact on social media only with friends they know. (Flags: Followers living more than 10 miles away, with significantly older birth dates, LinkedIn users following young teens.)

 Don't allow teachers and children to friend each other.
Don't allow teachers and children to friend each other.

 By age 18, start a dialogue, "How can my continued involvement in your social media best set you up for success?"
By age 18, start a dialogue, "How can my continued involvement in your social media best set you up for success?"
| | | | | | | | | | | | Advertisement
| | |
| | | print story
Before you print this article, please remember that it will remain in our archive for you to visit anytime.
download pdf
(use the pdf document for best printing results!) | | | Comments | | |
| | | | | | | | | | | | | | | | |


